
Researchers at the Citizen Lab from the University of Toronto’s Munk School have published a new report explaining how a zero-click exploit of iPhone software was possible and who was targeted. We first learned about the exploit and the mysterious company behind it last year. QuaDream, which sells spyware, remains in business.
Readers may be familiar with the Israeli company “NSO Group” and its Pegasus spyware. Apple is suing NSO Group for “abuse and harm” to its users. Companies like NSO Group sell spyware to clients, including governments that exploit security holes in iPhone and Android software.
QuaDream, which is responsible for targeting the iOS 14 zero-click exploit, is similar to NSO Group but maintains a much smaller public presence. As Citizen Lab puts it, QuaDream does not have extensive media exposure, nor does it have a website or social media accounts.
QuaDream does have legal issues of its own, however. The company is in a legal dispute with a firm based in Cyprus called InReach. The court battle has exposed information about QuaDream that was previously not public.
In the report, Citizen Lab describes key individuals connected to each company. This includes a former Israeli military official, Ian Dabelstein, and a California-based Israeli businessman, Roy Galsberg Keller.
ENDOFDAYS and the Ectoplasm Factor
Despite the dubious and paywalled headline “New Spyware Firm Said to Have Helped Hack iPhones Around the Globe” from Wall Street Journal, the news of the day is primarily that Citizen Lab has shared its analysis of the iOS exploit reported by Reuters in February 2022.
While the exploit itself is not new, the firm behind it continues to sell spyware software to clients willing to pay up.
ENDOFDAYS, as Citizen Lab calls the iOS 14 exploit, used invisible calendar event invites for overlapping events in the past.
“The malicious calendar events have additional distinctive characteristics that appear to always be the same,” says Citizen Lab. “The .ics file contains invitations to two overlapping events that are backdated. On iOS 14, any iCloud calendar invitation with a backdated time received by the phone is automatically processed and added to the user’s calendar with no user-facing prompt or notification. We are unsure why the events are overlapping, though there may be a specific behaviour triggered by overlapping events.”
The exploit is believed to have been used between January 2021 and November 2021.
Microsoft Threat Intelligence assisted Citizen Lab in understanding what QuaDream spyware could do once an iPhone was infiltrated through the zero-click exploit.
Microsoft Threat Intelligence shared with the Citizen Lab two samples of iOS spyware that they call KingsPawn, and attribute to QuaDream with high confidence.
We subsequently analysed these binaries, seeking to develop indicators that could be used to identify a device compromised with QuaDream spyware.
The list of identified QuaDream spyware functionality includes recording calls and microphones, tracking location and taking photos, and even generating iCloud 2FA passwords.
Where is this happening?
“We found that the spyware also contains a self-destruct feature that cleans up various traces left behind by the spyware itself. Our analysis of the self-destruct feature revealed a process name used by the spyware, which we discovered on victim devices,” says Citizen Lab.
One of the two spyware samples “sometimes leaves traces behind on infected devices after the spyware is removed” that Citizen Lab calls the Ectoplasm Factor.
“We omit discussion of the Ectoplasm Factor from our report, as we believe this may be useful for tracking QuaDream’s spyware going forward.”
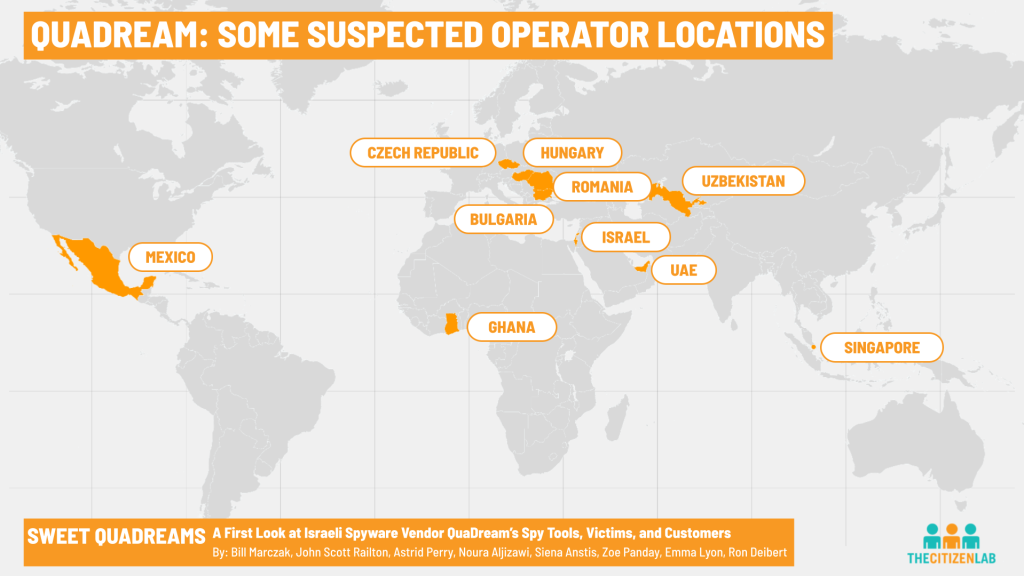
The report also provides an analysis of who is being targeted and which countries are cause for concern.
Based on an analysis of samples shared with us by Microsoft Threat Intelligence, we developed indicators that enabled us to identify at least five civil society victims of QuaDream’s spyware and exploits in North America, Central Asia, Southeast Asia, Europe, and the Middle East. Victims include journalists, political opposition figures, and an NGO worker. We are not naming the victims at this time.
What you should know
While an update to iOS 14 eliminated the zero-click exploit that QuaDream customers targeted, Apple has been more aggressive about preventing repeat occurrences with unknown security holes.
Namely, Apple added a security option in iOS 16 called Lockdown Mode. Any user can enable Lockdown Mode via the Settings app. When using Lockdown Mode, a number of changes are made to prevent spyware from affecting your phone:
- Messages: Most message attachment types other than images are blocked. Some features, like link previews, are disabled.
- Web browsing: Certain complex web technologies, like just-in-time (JIT) JavaScript compilation, are disabled unless the user excludes a trusted site from Lockdown Mode.
- Apple services: Incoming invitations and service requests, including FaceTime calls, are blocked if the user has not previously sent the initiator a call or request.
- FaceTime: Incoming FaceTime calls from people you have not previously called are blocked.
- Shared albums will be removed from the Photos app, and new Shared albums invitations will be blocked.
- Wired connections with a computer or accessory are blocked when iPhone is locked.
- Configuration profiles cannot be installed, and the device cannot enroll in mobile device management (MDM) while Lockdown Mode is turned on.
Apple also now alerts customers who may have been targeted by spyware firms.
Additionally, Apple donated $10 million to a nonprofit called The Dignity and Justice Fund. The group is using the money to fund a number of efforts:
- Building organizational capacity and increasing field coordination of new and existing civil society cybersecurity research and advocacy groups.
- Supporting the development of standardized forensic methods to detect and confirm spyware infiltration that meets evidentiary standards.
- Enabling civil society to more effectively partner with device manufacturers, software developers, commercial security firms, and other relevant companies to identify and address vulnerabilities.
- Increasing awareness among investors, journalists, and policymakers about the global mercenary spyware industry.
- Building the capacity of human rights defenders to identify and respond to spyware attacks, including security audits for organizations that face heightened threats to their networks.
Read the full Citizen Lab report to learn more about the results of research from studying QuaDream and the iOS 14 exploit.
Add 9to5Mac to your Google News feed.
FTC: We use income earning auto affiliate links. More.






