
Apple introduced System Integrity Protection (SIP) with OS X El Capitan in 2015, and it essentially adds multiple layers of security that blocks apps from accessing and modifying system files at a root level. While users can manually disable this feature, it’s not exactly easy to do so. But Microsoft found an exploit that could let attackers bypass SIP.
Microsoft details how it found the ‘Migraine’ exploit in macOS
As the company shared on its Security blog, a vulnerability named “Migraine” could bypass macOS’ System Integrity Protection and lead to arbitrary code execution on a device. The exploit is so named because it’s related to the macOS Migration Assistant, a native tool that helps users move data from a Mac or Windows PC to another Mac.
As Microsoft explained, bypassing SIP can lead to “serious consequences,” since this gives attackers access to all system files, which makes it easy to install malware and rootkits. The exploit was able to do this using a special entitlement designed to give unrestricted root access to the Migration Assistant app.
In a normal situation, the Migration Assistant tool is only accessible during the setup process of a new user account, which means that hackers not only need to force a complete system sign-out, but also need to have physical access to the computer. But to demonstrate the potential risk of this exploit, Microsoft showed that there was a way to take advantage of it without worrying about the limitations listed before.
Here’s how it works
Microsoft has modified the Migration Assistant utility to run without logging the user off. But modifying the app caused it to crash due to a codesign failure. What the security researchers then did was to run Setup Assistant (the app that guides the user through the first setup of a Mac) in debug mode, so that it would ignore the fact that Migration Assistant had been modified and lacked a valid signature.
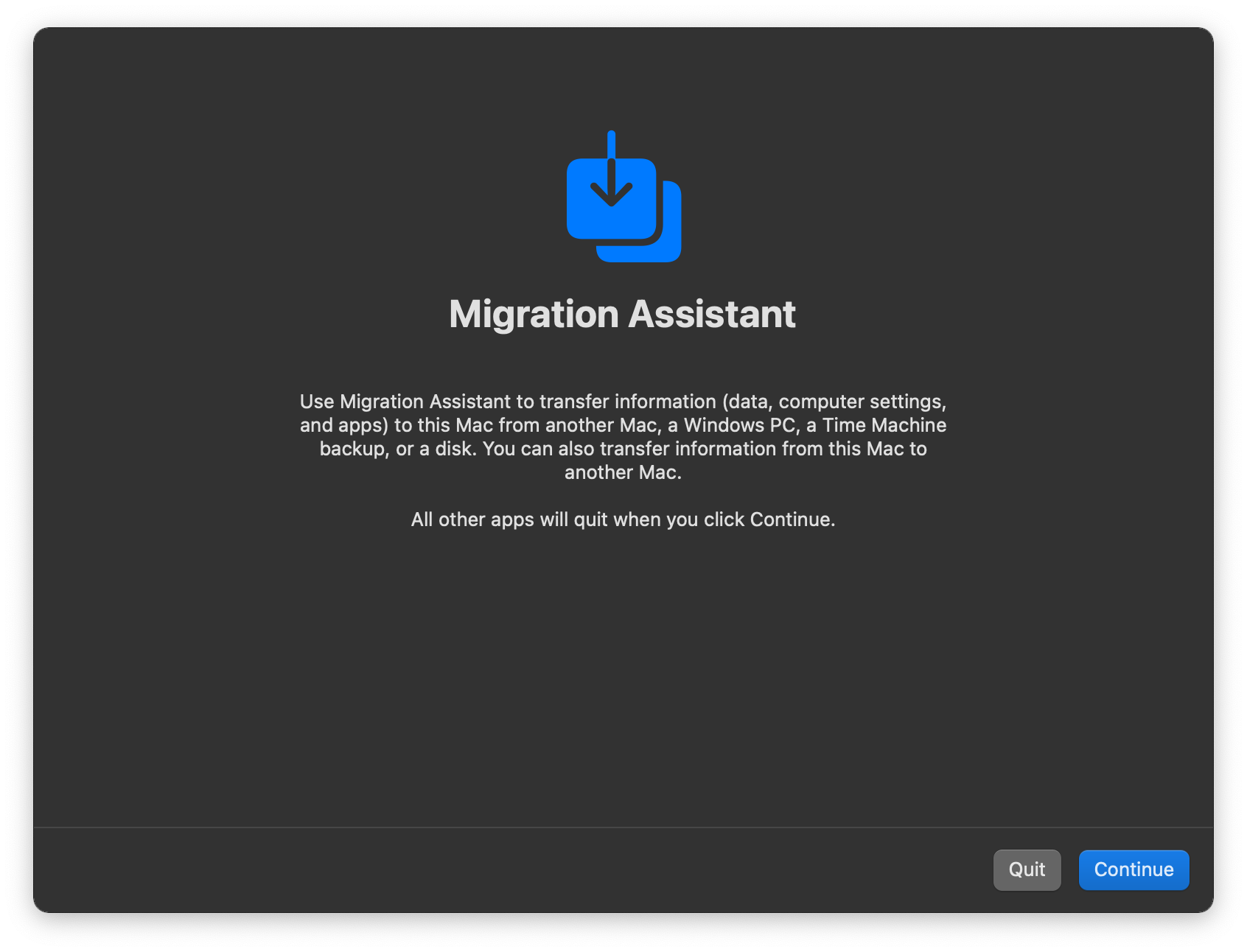
Since Setup Assistant was running in debug mode, the researchers could easily skip the steps of the setup process and jump straight to Migration Assistant. But even running in the macOS environment, this would still require having a disk to be restored and interaction with the interface.
To take the exploit even further, Microsoft has created a small 1GB Time Machine backup that could have malware on it. So the researchers created an AppleScript that automatically mounted this backup and interacted with the Migration Assistant interface without the user even noticing. As a result, the Mac would import the data from that malicious backup.
Should you be worried?
Luckily, you don’t have to worry if your Mac is running the latest version of macOS Ventura. That’s because Microsoft informed Apple about the exploit, which was fixed with the macOS 13.4 update – released on May 18 to the public. Apple thanked the Microsoft researchers on its security webpage.
If you haven’t updated your Mac yet, make sure you install the latest version of macOS as soon as possible by going to System Settings > General > Software Update.
Add 9to5Mac to your Google News feed.
FTC: We use income earning auto affiliate links. More.







