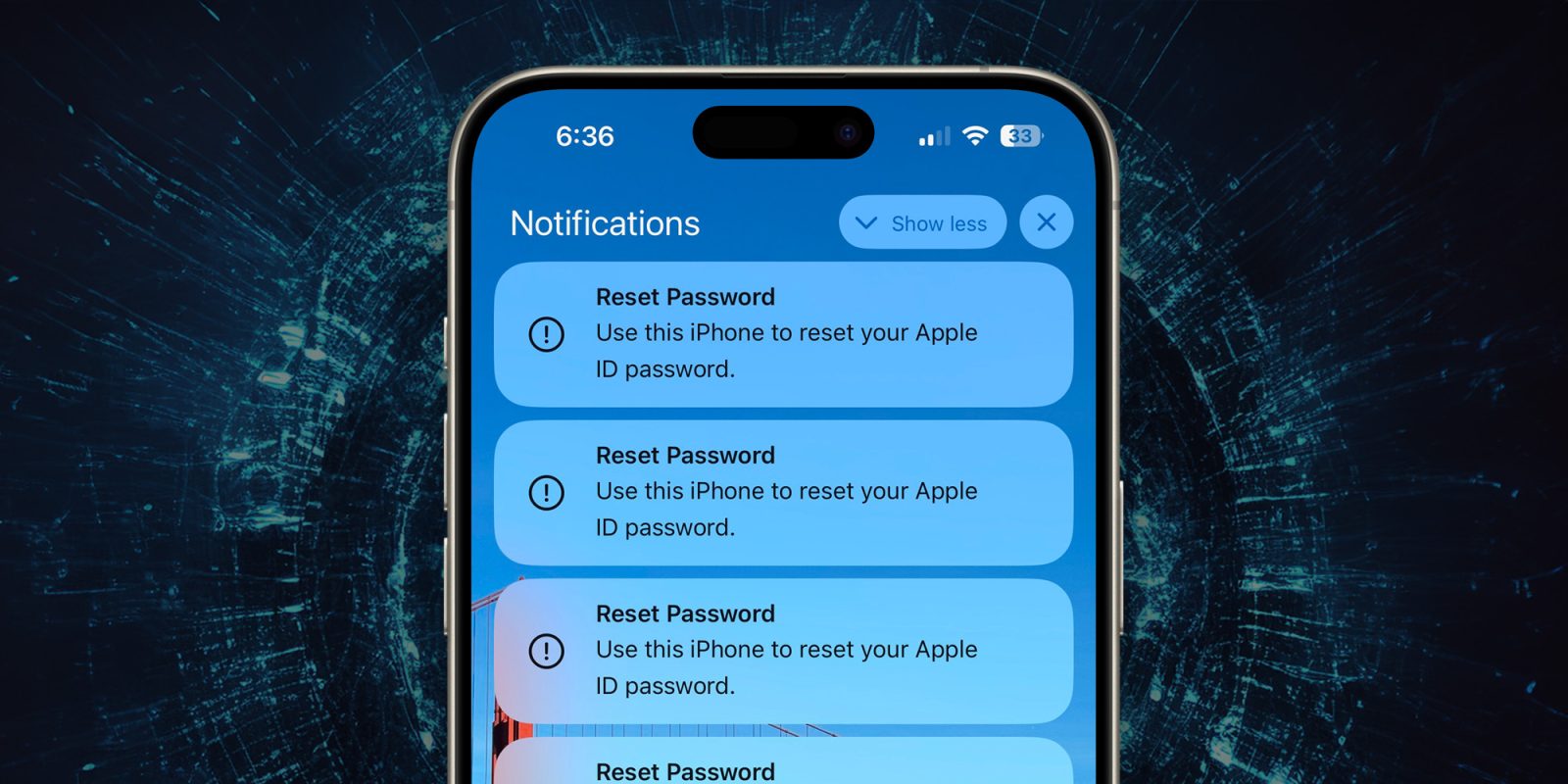
There are many known phishing attacks that target users of Apple devices to gain access to their Apple ID. However, a new “elaborate” attack uses a bug in the Apple ID password reset feature with “push bombing” or “MFA fatigue” techniques to flood Apple devices with password reset requests.
New phishing attack tries to convince users to reset their Apple ID password
As reported by Krebs on Security, entrepreneur Parth Patel was one of the victims of the new sophisticated phishing attack. Patel explained in a post on X that his iPhone and other Apple devices suddenly “started blowing up with Reset Password notifications.” However, since this is a system-level alert, it becomes impossible to use the device until you interact with it.
According to Patel, he was prompted by more than 100 requests to reset his Apple ID password. But the attack didn’t stop there. About 15 minutes later, the user received a call from someone spoofing the official Apple Support phone number.
“I was obviously still on guard, so I asked them to validate a ton of information about me, before answering any of their questions,” Patel said. To gain the victim’s trust, the person pretending to work for Apple Support shared multiple correct personal details, such as email, phone number, and current billing address.
Luckily, Patel was able to confirm that the call was a scam after asking the person to confirm his name. “I was tipped off that they used my data from People Data Labs in real time to validate a ton of information. Despite correctly stating all of my data, the phishers thought my name was Anthony S.”
For those unfamiliar, People Data Labs is a platform that collects and sells personal data. The platform was the target of a huge leak in 2019 that exposed around 1.2 billion records.
Finally the last thing they asked for was an OTP that explicitly says “Don’t share it with anyone”.
Hitting approve in the first reset notification spam attack OR sharing this code would’ve pwned me. pic.twitter.com/RQHRUre5ds
— Parth (@parth220_) March 23, 2024
What the attackers want is to convince the victims that something is wrong and that they need to share the code sent by Apple to reset their password. Of course, if the victim shares this code with someone else, that person can gain full access to the Apple ID.
Krebs on Security spoke to other Apple device users who were also targeted by the same phishing attack. In all cases, they were spammed with prompts to reset their Apple ID password and then received a call from fake Apple Support minutes or days later. It’s worth noting that Apple never calls users unless requested by the users themselves on its website or app.
Apple is yet to comment on the matter or release an update that prevents attackers from sending multiple password reset requests. For now, the best way to prevent attacks like this is to never share the code to reset your Apple ID password with other people.
Read also
- Security Bite: Jamf warns cyber hygiene among many Apple-using businesses is ‘abysmal’
- Here’s how to protect against ‘GoldPickaxe’, the first iPhone trojan
Add 9to5Mac to your Google News feed.
FTC: We use income earning auto affiliate links. More.







